The Telesploit solution consists of three distinct parts: the Telesploit server, the Telesploit relay, and an SSH capable client (Telesploit Client).
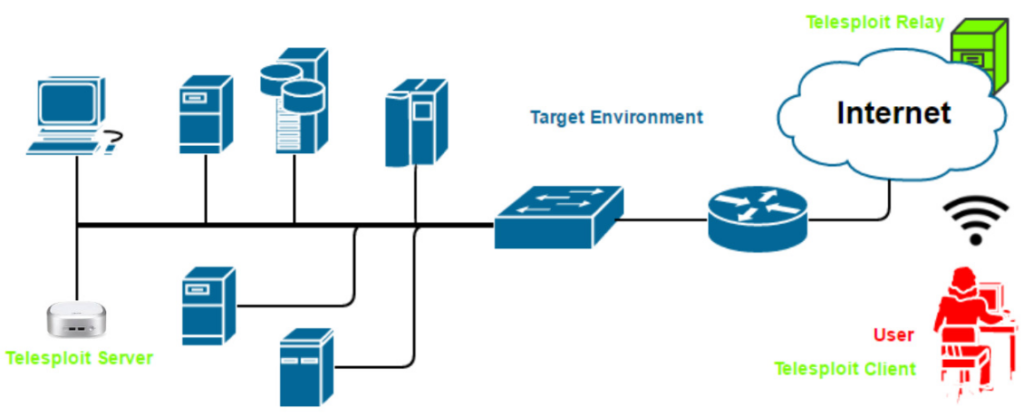
Telesploit Server
The server runs a Linux penetration testing platform and is deployed within the target environment. Once network connectivity and power have been applied to the device, it will automatically connect to its assigned Telesploit relay and, in its default configuration, create TLS encapsulated reverse SSH tunnels. These connections provide access to a console (SSH), remote desktop (VNC), web proxy (Squid), and many other applications on the Telesploit server.
Telesploit Relay
The relay runs in the cloud and provides secure access to the Telesploit server from Internet-connected clients using SSH key-based authentication. The relay includes pre-configured IRC, Rocket.Chat, and Squid servers for team-based communication, collaboration, and bypassing restrictive outbound controls from the environment where the Telesploit server is deployed.
Telesploit Client
The client connects to the Telesploit server via the relay. Penetration testing tools, such as Metasploit, can then be run directly from the server within the target environment or proxied through the established connections. The client can be any SSH enabled device, but will typically be the user’s computer or laptop.



